Karl Robinson
June 25, 2021
Karl is CEO and Co-Founder of Logicata – he’s an AWS Community Builder in the Cloud Operations category, and AWS Certified to Solutions Architect Professional level. Knowledgeable, informal, and approachable, Karl has founded, grown, and sold internet and cloud-hosting companies.

We all know how powerful AWS is and how everything is nicely automated. Launching a new Windows-based instance on EC2 has undoubtedly been a smooth experience for most of you.
However, never forget that the AWS platform, like any software, is not bug-free.
In fact, at the time of writing, our very own CTO Adriano Cataluddi discovered and reported an EC2 Windows Password Bug, which prevents users from retrieving the Administrator password on Windows 2019 instances created using the official AWS AMI. This seems to affect only the latest generation instances on AWS Nitro virtualization (T3, C5, etc.)
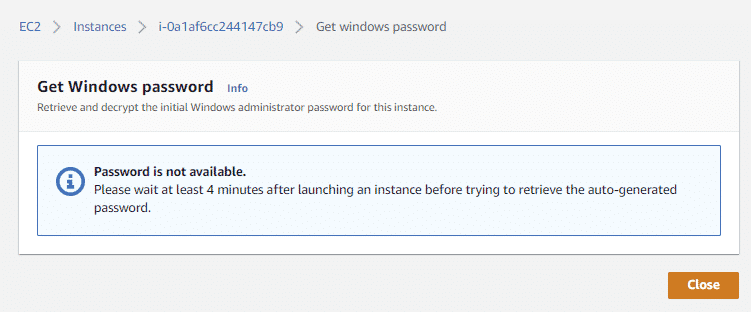
By provisioning a Windows instance, there’s a chance that you may have to wait forever for a password that will never be delivered, while only getting the following error message:
Password is not available.
Please wait at least 4 minutes after launching an instance before trying to retrieve the auto-generated password.
When this happens, even the following AWS CLI command will fail, returning an empty string:
aws ec2 get-password-data --instance-id <instance_id> --priv-launch-key key.pem
At the time of writing, AWS engineers have acknowledged the issue and are working on the resolution. In the meantime if you, like us, are in a hurry and need to get into your instance, here is a solution you might appreciate.
The Logicata Solution
First, you’ll need the private key you chose when launching your instance. If you generated a new one, please download it. This guide assumes you have such a key inside a file called WindowsCredentials.pem.
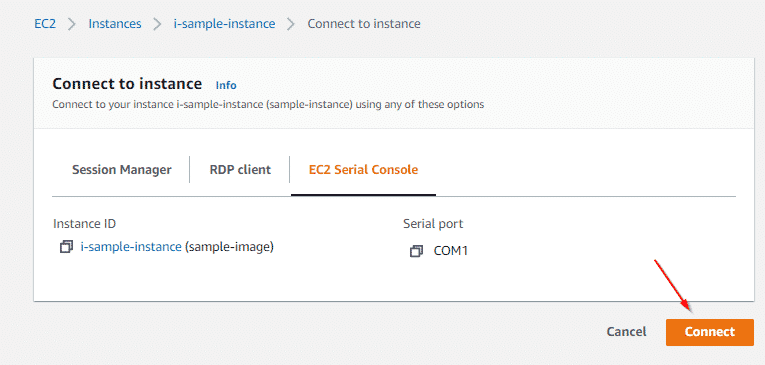
Then, in the EC2 console, select your instance, right-click and choose Connect. You will see the following window.
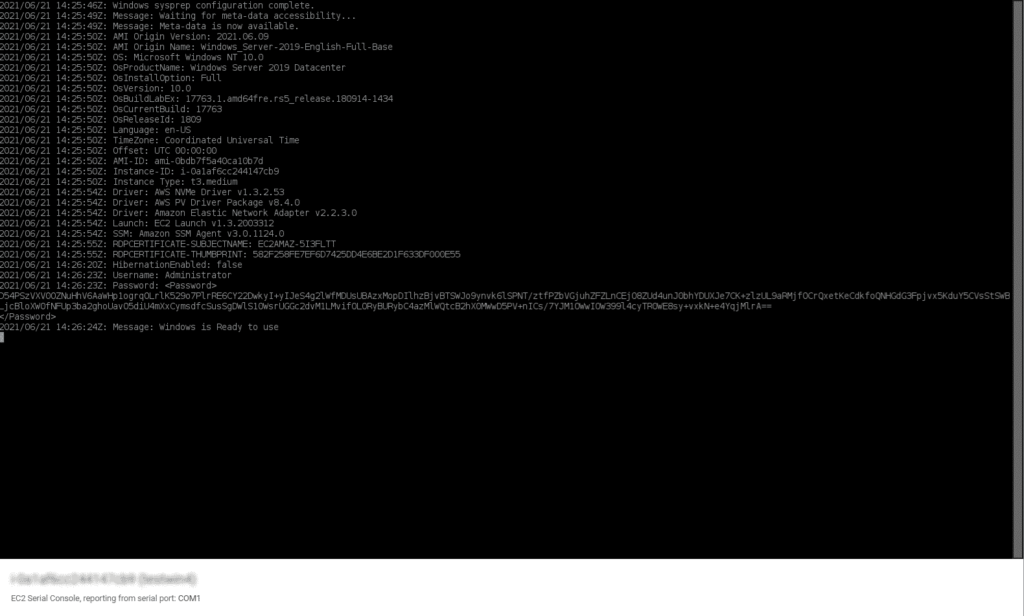
Once there, select the EC2 Serial Console tab and then the Connect orange button. You will access the EC2 Serial Console and see an output like the following:
You’ll notice a long string wrapped inside a tag, like the following:
[…] 2021/06/18 15:30:22Z Password: d3L0ajmGOk6VrUsT1lIu3Y3obKZsIvhXCjFh1iv90LIsWGsJ1ckZUwWqjyJW0TMPWWWQLssD6AVtif57QpOa0ekScOcNhHawvrbCLxz1SV8Lqz8Pcr7Uev8019EaYksck8momsG2FMnhHwE4sQkOhmsE1ALQtOsUN+mdtFoTeGpwI2jPTUyrAiNLX67NOVSMiNkIfmmjlBJg0fsjJNEG9tLiwxmpnBt4g5XubwHz7xybLh2CghKW3djou/i41G34JVTHf8OPQmPDaAuyd8LCg8ERJ48j9G/i3jlkjr4DWscRWT7IVPMuS6ZMp8yfedcmm2Mjhh9HRCYZrvGcKgbN1A==
Select the string inside the tag and put inside a file called source.txt. So, in our example, the source.txt will contain the following:
d3L0ajmGOk6VrUsT1lIu3Y3obKZsIvhXCjFh1iv90LIsWGsJ1ckZUwWqjyJ W0TMPWWWQLssD6AVtif57QpOa0ekScOcNhHawvrbCLxz1SV8Lqz8Pcr7Uev 8019EaYksck8momsG2FMnhHwE4sQkOhmsE1ALQtOsUN+mdtFoTeGpwI2jPTU yrAiNLX67NOVSMiNkIfmmjlBJg0fsjJNEG9tLiwxmpnBt4g5XubwHz7xybLh 2CghKW3djou/i41G34JVTHf8OPQmPDaAuyd8LCg8ERJ48j9G/i3jlkjr4DWs cRWT7IVPMuS6ZMp8yfedcmm2Mjhh9HRCYZrvGcKgbN1A==
Then run the following commands:
cat source.txt | tr -d 'n' | base64 -d > password.bin
openssl rsautl -decrypt -in password.bin -out password.txt -inkey ./WindowsCredentials.pem
Now the file password.txt will contain your Administrator password.
What a shame we only found out about the latest AWS Bug Bounty program after finding this bug!
I hope you find this useful. Every day, Logicata helps many organisations and professionals stay focused on development and while we enable them to have a better experience in the cloud. To improve your cloud journey, contact us.